 |
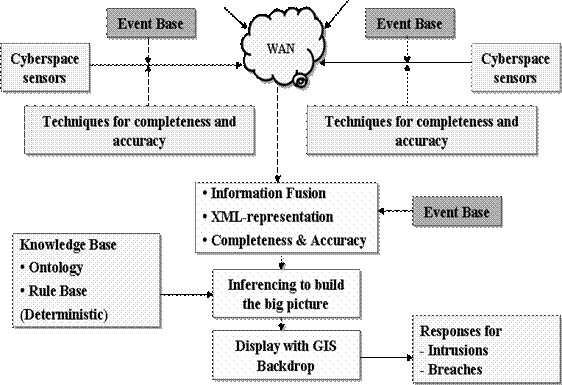
| A figurative display of integrated cyberspace intrusion detection system. |
By Anantha Krishnan M
Express News Service
Express News Service
Bangalore: Defence preparedness of any nation is widely assessed often in terms of visible assets with little authentic knowledge available in the public domain. While armed forces world over preferred not to speak or let others speak about the Information Technology (IT) strengths, one often read reports of cyber thefts, attacks and loopholes in so-called secure firewalls. While India has been prone to cyber vandalisms in the past, silent IT missions have been running concurrently to aid India’s defence preparedness.
Sources who agreed to part with information on this front to Express said that during conflicts, the side that has superior access to accurate and timely information has a clear edge over its adversary. “Information gathering, processing, and delivering systems and their effective exploitation in the battlefield are vital for prevailing in the end. Collectively these computerised and networked defence systems make the battlefield digital in nature and entail the need to protect the cyberspace associated with them,” sources with Bangalore-based Centre for Artificial Intelligence and Robotics (CAIR), said.
Given the density and complexity of computerisation in these systems, the corresponding cyberspace acquires a physical reality of its own. Briefly, this cyberspace of the defence systems is the abode of the critical information gathered from the sensors and processed and forwarded to the weapons.
“The twin objectives of the security of this space are to keep its integrity intact and to keep the information housed therein confidential, untampered, and available. Preventive solutions exist for ensuring authentication and access control on the one hand and for encrypting storage and communications of the information concerned on the other. However, these solutions cannot assure complete security especially where human operators are involved and where the defence systems are open in nature requiring interactions with unknown and unpredictable frontiers such as a battlefield,” sources said.
One of the basic methods to check for intrusions is to keep a watch on the integrity values of the committed and free regions of the cyberspace. The committed regions house information and software in the form of files. “Based on a careful sampling of these files, corresponding hashes or checksums may be calculated in clean state and kept as references. Subsequently on a periodic basis, the instantaneous values of the hashes of the select subset of the files may be computed and checked against the references. The unexpected changes, if any, can be an indication of an intrusion,” sources said.
In order to look at aggregate activities of a number of computing hosts and network devices, the technique is to analyse the traffic emanating from or going towards them over gateway-like points. This technique is the basis of many network intrusion detection systems. “There are two generic methods implemented in these systems; one is based on ‘signatures’ of attacks to gain entry into the cyberspaces of target systems, and the other is to identify anomalies in traffic patterns based on statistics or rules,” sources said.
Based on needs, CAIR has developed an IP traffic-based Intrusion Sensing System for Enterprise Networks that can analyze traffic data for possible attacks originating from outside an organization.
Sources who agreed to part with information on this front to Express said that during conflicts, the side that has superior access to accurate and timely information has a clear edge over its adversary. “Information gathering, processing, and delivering systems and their effective exploitation in the battlefield are vital for prevailing in the end. Collectively these computerised and networked defence systems make the battlefield digital in nature and entail the need to protect the cyberspace associated with them,” sources with Bangalore-based Centre for Artificial Intelligence and Robotics (CAIR), said.
Given the density and complexity of computerisation in these systems, the corresponding cyberspace acquires a physical reality of its own. Briefly, this cyberspace of the defence systems is the abode of the critical information gathered from the sensors and processed and forwarded to the weapons.
“The twin objectives of the security of this space are to keep its integrity intact and to keep the information housed therein confidential, untampered, and available. Preventive solutions exist for ensuring authentication and access control on the one hand and for encrypting storage and communications of the information concerned on the other. However, these solutions cannot assure complete security especially where human operators are involved and where the defence systems are open in nature requiring interactions with unknown and unpredictable frontiers such as a battlefield,” sources said.
One of the basic methods to check for intrusions is to keep a watch on the integrity values of the committed and free regions of the cyberspace. The committed regions house information and software in the form of files. “Based on a careful sampling of these files, corresponding hashes or checksums may be calculated in clean state and kept as references. Subsequently on a periodic basis, the instantaneous values of the hashes of the select subset of the files may be computed and checked against the references. The unexpected changes, if any, can be an indication of an intrusion,” sources said.
In order to look at aggregate activities of a number of computing hosts and network devices, the technique is to analyse the traffic emanating from or going towards them over gateway-like points. This technique is the basis of many network intrusion detection systems. “There are two generic methods implemented in these systems; one is based on ‘signatures’ of attacks to gain entry into the cyberspaces of target systems, and the other is to identify anomalies in traffic patterns based on statistics or rules,” sources said.
Based on needs, CAIR has developed an IP traffic-based Intrusion Sensing System for Enterprise Networks that can analyze traffic data for possible attacks originating from outside an organization.
Copyrigth@The New Indian Express
Part-3 tomorrow: Robotics for low-intense conflict operations)






















